The dark web is neither the origin nor the entirety of cybercrime, but it is the connective that accelerates it. With strong anonymity, frictionless monetization (cryptocurrencies, mixers, P2P cash-outs), and resilient communities (forums, markets, leak sites), the dark web shortens the time from exploit to revenue.
Over the last two years, international operations have repeatedly disrupted flagship hubs, but the ecosystem keeps adapting. Meanwhile, measurable harm, stolen data, ransomware incidents, mass credential dumps, and crypto thefts continue to rise in several categories.
Your email could be compromised.
Scan it on the dark web for free – no signup required.
We will discuss today’s dark-web-enabled threat economy using current statistics, recent cases, and enforcement shifts. We will also discuss what might be the future of dark web crimes and what could be done to keep yourself secure.
What We Mean by “Dark Web?”
The dark web is a part of the internet that you can only reach with special tools, like the Tor browser. It’s designed to hide who you are and where you’re connecting from. Tor, the most widely used system, supports millions of users every day through thousands of hidden sites and servers. People use it for both legal and illegal purposes, and Tor’s own usage data gives the most reliable picture of its scale.
Dark Web Cybercrime Statistics 2024–2025: The Growing Economy
Cybercrime on the dark web is growing more sophisticated, and the numbers prove it. Looking at ransomware payouts, stolen data, and crypto-driven drug sales, the illicit economy is thriving in 2024–2025.
1) Crypto-Enabled Crime and Darknet Commerce
Chainalysis estimates ~$40.9B to be identified illicit addresses (lower-bound), with darknet markets and fraud shops taking a smaller share than other categories. Inflows to DNMs were just over $2B (BTC on-chain) in 2024, with fraud shops around $225M, reflecting pressure from enforcement and market fragmentation.
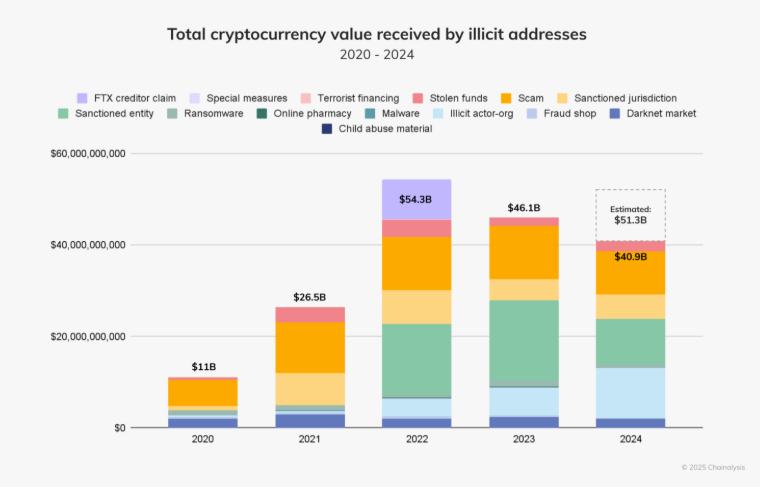
TRM Labs reports crypto-enabled online drug sales grew ~19% YoY into ~$2.4B, even as 42% fewer new darknet markets launched and a higher fraction were Monero-only. This reveals a shift from centralized megamarkets to more specialized, privacy-focused venues.
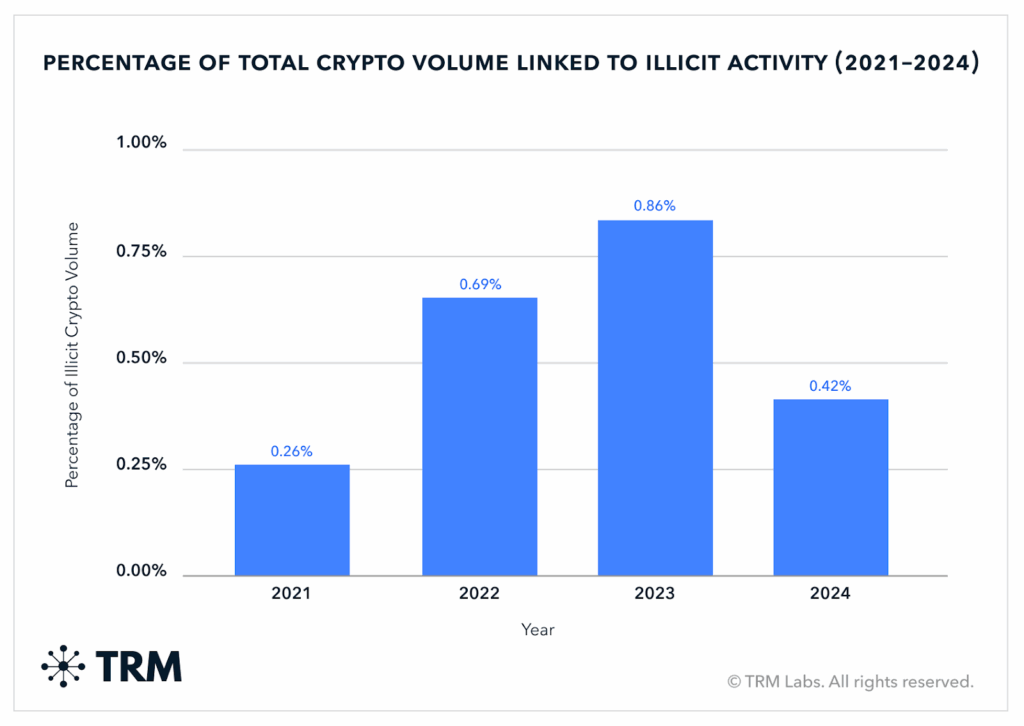
2) Ransomware and Leak-Site Ecosystems
Ransomware remains the lead monetization model connecting initial access brokers, data-leak sites, and victim negotiation portals, nearly all of which are reachable via Tor.
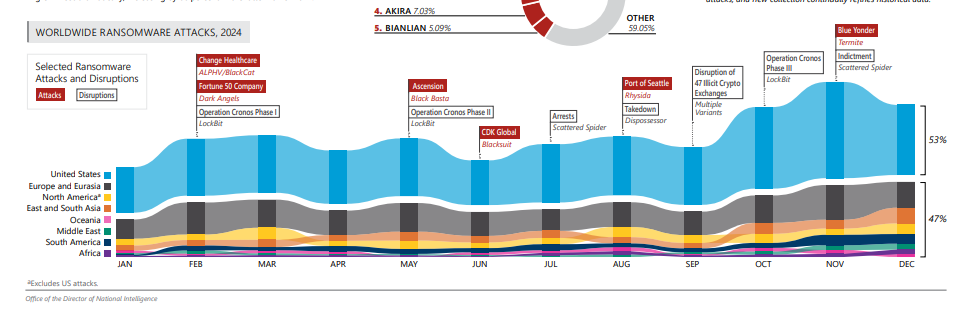
Global actions like Operation Cronos (2024) disrupted LockBit (infrastructure seizure, arrests, unmasking of alleged operators), but the broader affiliate-driven ecosystem persists. The U.S. Intelligence Community’s 2024 assessment even cites a record $75M ransom paid to a non-LockBit group (Dark Angels), highlighting high-end payouts despite takedowns.
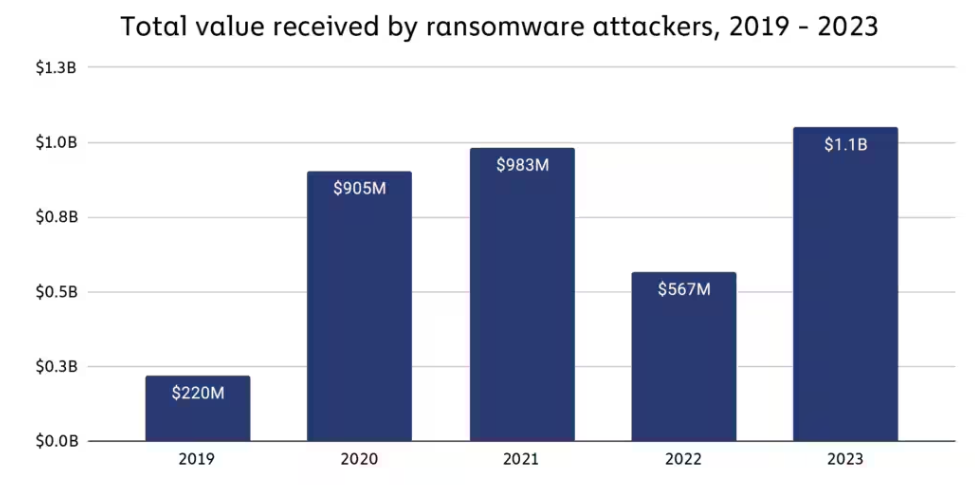
3) Identity Data and Credential Markets
Credentials are the currency of cybercrime. Fortinet notes 100B+ compromised records shared on underground forums in 2024 (up ~42% YoY), fueling credential-stuffing and account-takeover at scale.
IBM X-Force corroborates a surge in infostealer-delivered phishing (+84%) and a corresponding increase in stolen credentials for sale.
4) Botnets, Loaders, and Crime-as-a-Service (CaaS)
Operation Endgame (2024–2025) dismantled portions of the “ransomware kill chain” by targeting droppers/initial access malware and their infrastructure across hundreds of servers, seizing €21.2M in crypto, and issuing warrants for dozens of suspects. This hits the supply side of CaaS that feeds dark-web markets and leak sites.

Major Dark-Web-Linked Events (2024–2025) You Should Know
The past two years have been marked by major law-enforcement crackdowns and high-profile cybercrime cases tied to the dark web. Understanding these milestones helps explain where dark-web cybercrime is headed next.
- Operation Cronos vs. LockBit (Feb–May 2024)
Infrastructure seized; multiple arrests; identity of alleged LockBit leader publicized. Trust erosion among affiliates led to code leaks and observable regrouping attempts.
- BreachForums Seizures and Fallout (May 2024, 2025)
In May 2024, the FBI and partners seized BreachForums (Tor and clearnet). In 2025, arrests of additional admins (incl. links to “ShinyHunters”) and claims of a MyBB 0-day infiltration further destabilized the community, pushing sellers/buyers to alternative forums and private channels.

- Operation Endgame Continues (2024–2025)
Multinational actions targeted droppers/botnets used to deliver ransomware and steal credentials, removing 300+ servers and neutralizing 650 domains in a May 2025 phase alone. This hampers initial access brokers who advertise on forums.
- Explosive Growth in Mass Credential Exposure (2024–2025)
Industry telemetry shows record credential leaks and combo-list trading across underground forums. Several 2025 “mega-dumps” (some exceeding prior volumes) further lowered the barrier to ATO, business email compromise, and lateral movement.
- CSAM Networks and Tor (Aug 2025 spotlight)
Investigative reporting highlighted persistent CSAM communities on Tor and the difficulty of technical interventions without undermining anonymity, highlighting the policy tension between privacy infrastructure and abuse mitigation.
How the Dark Web Powers the Global Cybercrime Supply Chain
The dark web acts as the backbone of today’s cybercrime economy, connecting hackers, sellers, and buyers worldwide. Everything has its place in this hidden ecosystem.
1) Access and Tooling
Initial Access Brokers (IABs) advertise RDP/VPN credentials, web-shell footholds, and cloud keys. Malware-as-a-Service sellers provide loaders, stealers, and exploit kits, with zero-day chatter and PoCs circulating in gated venues.
Fortinet’s 2025 report catalogs 331 zero-days discussed on darknet forums in 2024, with >30% offering fully functional exploits, a material boost to time-to-weaponization.
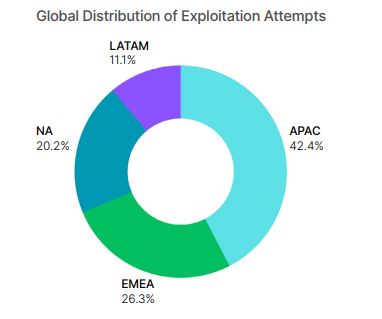
2) Monetization and Laundering
Ransomware-as-a-Service (RaaS) programs run leak portals on Tor, with affiliates handling intrusion and operators taking a cut.
Stablecoins, BTC, and especially Monero for DNM transactions, with mixer/bridge use for obfuscation. (Chainalysis and TRM data capture the magnitude, while also noting migration towards privacy-oriented rails.)
3) Distribution and Retention
Fraud shops resell credentials and PII; combo lists feed automated credential-stuffing and OTP-bypass kits; data-leak sites extort non-paying victims by publishing samples. Law-enforcement seizures disrupt, but content and actors often re-surface elsewhere.
Enforcement Is Getting Better—But So Are the Criminals
Global operations against dark-web crime have become more frequent and effective, taking down markets, ransomware gangs, and botnet networks. Yet, cybercriminals continue to adapt quickly, shifting to new platforms, privacy coins, and decentralized models.
Where Takedowns Work
- Shutting down servers and networks in operations like Cronos and Endgame makes it harder and more expensive for criminals to keep their dark-web platforms running. It also causes mistrust between market owners and their partners.
- Exposing the people behind these crimes, by naming operators publicly and seizing their money or assets, discourages others from joining and lowers confidence among existing members.
How Offenders Adapt
- When one dark-web forum is shut down, sellers quickly move to backup forums, encrypted messaging apps, or small, invite-only markets.
- More markets now use Monero only and rely on private payment methods, making transactions harder to trace.
- Instead of big marketplaces, criminals are turning to direct peer-to-peer deals or small hidden websites, which makes law-enforcement takedowns less effective.
Policy and Governance Trajectory Against the Dark Web
UN Convention against Cybercrime (adopted 24 Dec 2024): Aims to streamline cross-border evidence sharing and joint action against cybercrime, including offenses heavily facilitated by dark-web infrastructure. Human-rights groups have flagged due-process and free-expression concerns; implementation details in 2025–2026 will matter.
Broader adoption of Travel Rule controls for virtual assets could compress laundering options over time, particularly for centralized ramps, though DeFi, bridges, and privacy-coins remain challenging.
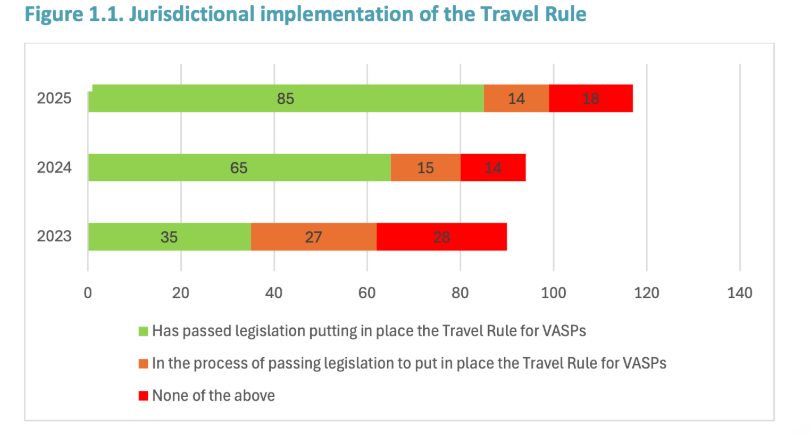
What Can Happen in the Future with the Dark Web: The Next 24 Months, Probably!
The dark web is not disappearing, it’s evolving. Over the next two years, expect new tactics like stronger use of privacy coins, AI-driven scams, and smaller, harder-to-track markets.
- Persistent Ransomware with Thinner Margins
Expect continued activity, but with more churn in affiliate programs and a tilt toward multi-extortion (data theft + DDoS + harassment) as insurance-driven defenses and takedowns squeeze payment rates. Leak-site attrition may rise as hosting and OPSEC get costlier.
- Privacy-First Payment Rails
More Monero-only markets and escrow variants; increased pressure on centralized mixers pushes laundering toward cross-chain bridges and decentralized mixers, complicating visibility for blockchain analytics.
- Commoditized Initial Access
Despite Endgame-style disruptions, IABs will keep thriving due to fresh credential supply (infostealers + MFA fatigue kits). Expect more turnkey intrusion bundles (access + playbooks + tooling + support).
- AI-Accelerated Fraud and Social Engineering
Deep-fake voice/video, synthetic IDs, and automated scam/fraud copy are already in circulation on closed forums. Availability will increase, lowering the barrier for mid-tier actors. (Multiple 2024–2025 threat-intel indices report sustained growth in these kits.)
- Regulatory Divergence
As UN and FATF frameworks harden, some jurisdictions will become permissive hubs for crypto laundering and bulletproof hosting, fragmenting enforcement outcomes. Expect more joint action weeks (Cronos/Endgame-style) to keep pressure on infrastructure.
Practical Risk-Reduction for Security Leaders
As dark-web threats grow, security leaders need actionable defenses, not just awareness.
1) Identity-First Defense
Assume credentials are exposed. Enforce phishing-resistant MFA (FIDO2/WebAuthn), device binding, and conditional access. Continuously check your domains in stealer logs and combo lists; rotate or step-up auth based on exposure. FortinetIBM
2) Prioritize Initial Access Controls
Harden public attack surface, segment remote access, and monitor for IAB-style listings of your org. Integrate dark-web monitoring with takedown workflows (where feasible) and incident playbooks referencing common loader families disrupted by Endgame.
3) Backstop Ransomware
Implement 3-2-1 backups with immutability, test restores quarterly, and isolate backup control planes. Prepare for data-theft-only extortion (even if encryption never triggers). Track leak-site mentions and enforce legal holds.
4) Crypto Exposure Management
If you operate crypto payments/treasury: integrate blockchain analytics for sanctions/illicit screening, assess exposure to mixers/bridges, and plan for Travel Rule compliance impacts across partners.
5) Supplier & Identity Risk
Continuously validate third-party SSO/MFA posture, vault hygiene (service accounts, API keys), and egress logging. Require breach-notification SLAs that include dark-web evidence handling.
6) Human-Centric Controls
Run adversarial simulations (phishing + MFA fatigue + deep-fake vishing). Train high-risk roles with live demos of stealer kits and data-broker posts to concretize risk.
Wrap Up
The dark web’s value to cybercriminals is structural, anonymity, liquidity, community, and resilience. 2024–2025 shows both sides escalating.
Security leaders should assume pervasive credential exposure, focus on breaking the initial-access → privilege → exfiltration → extortion chain, and instrument programs to detect exploitation before an actor reaches a leak site.
What’s in your hand? Managing your data so that it is not exploited on the dark web. Switch to PureVPN dark web monitor and keep a track of what’s exposed without your permission.
Frequently Asked Questions
It’s a force multiplier rather than the sole driver. The dark web enables distribution (forums/markets), monetization (RaaS, fraud shops), and resilience (onion hosting). However, many intrusions start on the clearnet (email, social, vulnerable apps) and only later enter dark-web channels for resale or extortion.
They disrupted it but didn’t end it. Cronos and Endgame raised costs and fractured communities, but affiliates regrouped. Net-new groups and rebrands appear, and payment behavior adapts. The goal is economic pressure and friction, not instant eradication.
Fewer new markets launched in 2024 and more require Monero; yet crypto-enabled drug sales still grew year-over-year, and 2024 DNM inflows were ~$2B. The model is shifting toward specialization and privacy, but not disappearing.
It standardizes cooperation and evidence handling across borders, accelerating mutual legal assistance for dark-web cases. Rights groups warn of overreach risks, so national implementations will determine the balance of enforcement and civil liberties.