The CIS Advisory reported that Google Chrome has several security issues. These severe vulnerabilities could allow hackers to run code on a person’s computer. If a hacker can exploit these vulnerabilities successfully, they could take control of the computer and install programs, access or delete files, or create new user accounts with complete control. People who use
Chrome with fewer privileges or permissions on their computers may be less affected than those with administrative access.
Technical details
The never exploited vulnerabilities with the greatest threat are:
Tactic: Initial Access (TA0001):
Technique: Drive-By Compromise (T1189):
- Out of Bounds Write in Swiftshader (CVE-2023-2929)
- Use after free in Extensions (CVE-2023-2930)
- Use after free in PDF (CVE-2023-2931, CVE-2023-2932, CVE-2023-2933)
- Out-of-bounds memory access in Mojo (CVE-2023-2934)
- Type Confusion in V8 (CVE-2023-2935, CVE-2023-2936)
- Inappropriate implementation in Picture In Picture (CVE-2023-2937, CVE-2023-2938)
- Insufficient data validation in Installer (CVE-2023-2939)
- Inappropriate implementation in Downloads (CVE-2023-2940)
- Inappropriate implementation in Extensions API (CVE-2023-2941)
Source: NIST
What arbitrary code executions could do?
If a hacker gets you through this arbitrary code execution, he can:
- Get unauthorized access
- Install malware
- Control your system
- Exploit other vulnerabilities
- Initiate network attacks
Who’s most affected?
Government:
Large and medium government entities: HIGH
Small entities: MEDIUM
Businesses:
Large and medium business entities: HIGH
Small business entities: MEDIUM
Home Users: LOW
Emergency update to fix a zero-day vulnerability
Steps you must take to be safe
- Apply the appropriate updates provided by Google to vulnerable systems promptly after conducting necessary testing. (M1051: Update Software)

- Ensure establishing and maintaining a documented vulnerability management process for enterprise assets, reviewing and updating the documentation annually or when significant enterprise changes may impact this safeguard. (Safeguard 7.1: Establish and Maintain a Vulnerability Management Process)
- Perform automated application patch management monthly or more frequently, applying application updates to enterprise assets through automated patch management. (Safeguard 7.4: Perform Automated Application Patch Management)
- Remediate identified vulnerabilities in software through processes and tools monthly or more frequently, based on the remediation process. (Safeguard 7.7: Remediate Detected Vulnerabilities)
- Ensure the use of only fully supported browsers and email clients in the enterprise, allowing only the latest versions provided by the vendor. (Safeguard 9.1: Ensure Use of Only Fully Supported Browsers and Email Clients)
- Implement the principle of least privilege for all systems and services. Run all software with non-privileged user accounts (without administrative privileges) to minimize the impact of a successful attack. (M1026: Privileged Account Management)
- Manage default accounts on enterprise assets and software, such as root, administrator, and other pre-configured vendor accounts. Examples include disabling default accounts or rendering them unusable. (Safeguard 4.7: Manage Default Accounts on Enterprise Assets and Software)
- Restrict administrator privileges to dedicated administrator accounts on enterprise assets. From the user’s primary non-privileged account, carry out general computing activities, such as internet browsing, email, and productivity suite use. (Safeguard 5.4: Restrict Administrator Privileges to Dedicated Administrator Accounts)
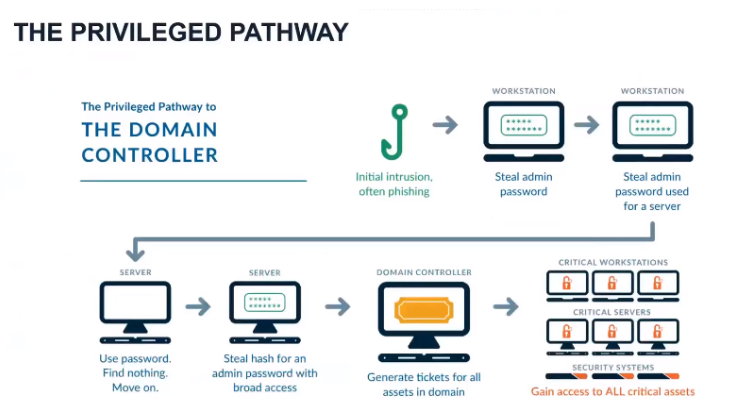
Source: CyberArk
- Restrict the execution of code to a virtual environment when on or in transit to an endpoint system. (M1048: Application Isolation and Sandboxing)
- Utilize capabilities to detect and block conditions indicating or leading to a software exploit. (M1050: Exploit Protection)
- Enable anti-exploitation features, where available, on enterprise assets and software, such as Microsoft® Data Execution Prevention (DEP), Windows® Defender Exploit Guard (WDEG), or Apple® System Integrity Protection (SIP) and Gatekeeper™. (Safeguard 10.5: Enable Anti-Exploitation Features)
- Implement restrictions on certain websites, block downloads/attachments, disable JavaScript, and restrict browser extensions, among other measures. (M1021: Restrict Web-Based Content)
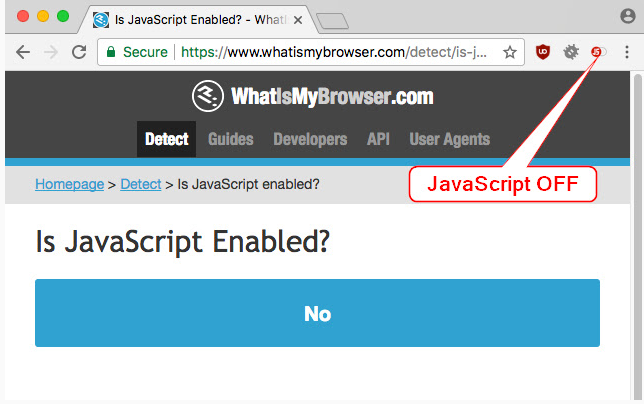
Source: Google
- Utilize DNS filtering services on all enterprise assets to block access to known malicious domains. (Safeguard 9.2: Use DNS Filtering Services)
- Maintain and enforce network-based URL filters to prevent enterprise assets from connecting to potentially malicious or unauthorized websites. This can be achieved through category-based filtering, reputation-based filtering, or the use of block lists. Apply these filters to all enterprise assets. (Safeguard 9.3: Maintain and Enforce Network-Based URL Filters)
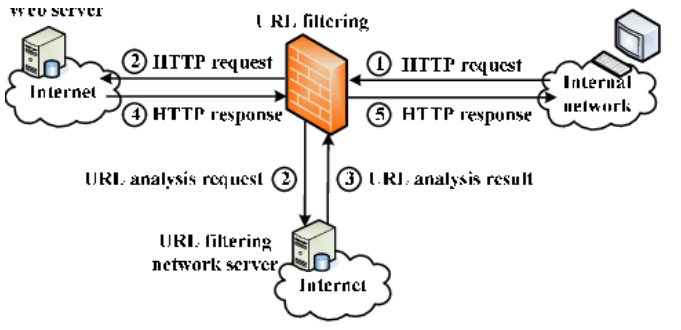
Source: Research Gate
- Block unnecessary file types attempting to enter the enterprise’s email gateway. (Safeguard 9.6: Block Unnecessary File Types)
What did we learn?
Educating and informing users about the risks associated with hypertext links in emails or attachments, especially from untrusted sources, is very important. Reminding them to avoid visiting untrusted websites or clicking on links provided by unknown or untrusted sources is also essential.
Organizations must establish and maintain a security awareness program to educate the workforce on secure interactions with enterprise assets and data. Conduct training at the time of hiring and at least once a year. Review and update the program’s content annually or when significant enterprise changes occur.
Be safe!



