Following the compromise of an Azure administrator’s account at an undisclosed organization, the threat actor known as UNC3944 utilised the serial console feature within Azure virtual machines to achieve complete administrative control. By exploiting this tool, the actor installed third-party remote access tools, maintained covert operations, and navigated victim environments undetected.
A recent analysis conducted by Mandiant researchers revealed how this financially motivated threat actor used legitimate Azure tools and functionalities, such as the serial console. Typically employed for troubleshooting purposes on Azure virtual machines, the serial console became a means for the attacker to execute their malicious activities.
- Using built-in tools in Living off the Land attacks has become increasingly prevalent, allowing them to evade detection more effectively.
- The innovative use of the serial console demonstrates that such attacks are no longer confined to the operating system layer.
History of UNC3944
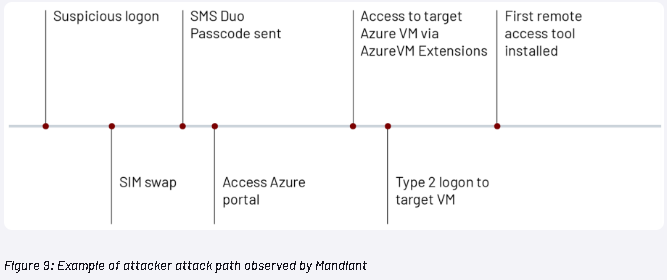
UNC3944, tracked by Mandiant since May 2022, has previously relied on techniques like
- SIM swapping,
- email and
- SMS phishing attacks and
- deployment of malicious signed drivers.
Their objective is data theft, and they often leverage compromised credentials of administrators or privileged accounts for initial access.
This attack employed SMS phishing, SIM swapping, and impersonation to deceive help desk agents into providing multi-factor reset codes via SMS. The specific methods used for SIM swapping need to be discovered by Mandiant.
The array of deception
Once the Azure administrator’s account was compromised, the attackers leveraged various privileges associated with administrative accounts. This included
- exporting user data within the tenant,
- gathering information about the Azure environment’s configuration, and
- creating or modifying accounts.
- Utilizing the serial console functionality, they accessed the administrative command prompt on an Azure VM, using the unique administration console feature that enables users to establish a connection to the operating system through the serial port and execute commands within it.
Courtesy: Mandiant
Microsoft’s authentication strength: How can it help in being secure
Authentication strength is a feature in Conditional Access control that lets administrators choose how people can prove who they are to access something. For instance, they can use methods that protect against phishing to access something important. But for something less critical, they can allow simpler and less secure ways like using a password and receiving a text message.
Authentication strengths can assist customers in various situations, including:
- Making it necessary to use particular ways of proving identity to access something important.
- Demanding a specific authentication method when a user performs a sensitive action within an application (alongside the authentication context of Conditional Access).
- Requiring users to utilize a specific authentication method when accessing sensitive applications from outside the company network.
- Mandating more secure authentication methods for users who are considered to be at a high risk.
- Imposing specific authentication methods for guest users accessing a shared resource (combined with settings for multiple tenants).
Footprints to follow
As attackers have become more adept at avoiding detection, Living off the Land attacks have become increasingly prevalent. These attacks involve leveraging pre-installed tools to carry out malicious activities. A recent example is the innovative use of the serial console by attackers, highlighting that these attacks are no longer confined to the operating system layer.
To address this growing threat, Mandiant, a prominent cybersecurity firm, advises organizations to implement certain measures to address this ever-increasing threats.
- One recommendation is to restrict access to remote administration channels, ensuring that only authorized personnel can utilize them.
- By limiting access, organizations can reduce the risk of attackers exploiting these channels for nefarious purposes.
- Mandiant suggests disabling SMS as a method of multifactor authentication (MFA) whenever feasible.
While SMS-based MFA has been widely adopted for its convenience, it is not considered as secure as other methods. Attackers have demonstrated the ability to compromise SMS-based authentication, making it vulnerable to interception or manipulation. To enhance security, organizations are encouraged to explore alternative MFA options that provide high protection against unauthorized access.
By implementing these precautions, organizations can fortify their defense against fileless attacks and reduce the chances of successful infiltration by adversaries.



