Another demonstration of a sandbox escape proof-of-concept (PoC) exploit has been published by a security analyst, Github, allowing the execution of unsecured code on a host that employs the VM2 sandbox.

Source: GitHub
Don’t know VM2, then read
The VM2 is a dedicated JavaScript sandbox extensively used by various software tools.
- Run and test suspicious code in an isolated environment, ensuring it cannot access the host’s system resources or external data.
- The library is frequently present in integrated development environments (IDEs),
- code editors,
- security tools, and
- a variety of pen-testing frameworks.
It is downloaded millions of times each month from the NPM package repository.
VM2 has had several serious sandboxes escape disclosures in the previous two weeks by different security researchers, enabling attackers to execute malicious code beyond the limits of the sandboxed environment.
The first sandbox escape vulnerability, identified as CVE-2023-29017, was discovered by Seongil Wi two weeks ago, with the most recent two (CVE-2023-29199 and CVE-2023-30547) discovered by Seung Hyun Lee.
In October 2022, researchers from Oxeye found another sandbox escape flaw, which is tracked as CVE-2022-36067.
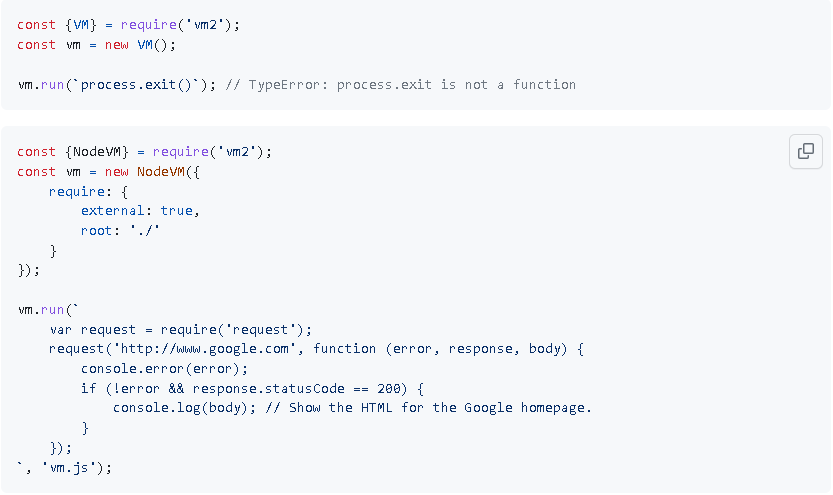
Technical analysis of VM2
VM2 is a sandbox that securely runs untrusted code with allowed Node’s built-in modules.
According to Github, VM2:
- Runs untrusted code securely in a single process with your code side by side
- Full control over the sandbox’s console output
- The sandbox has limited access to the process’s methods
- It is possible to require modules (built-in and external) from the sandbox
- You can limit access to certain (or all) built-in modules
- You can securely call methods and exchange data and callbacks between sandboxes
- Is immune to all known methods of attacks
- Transpiler support
It works:
- By using the internal VM module to create a secure context.
- By using Proxies to prevent escape from the sandbox.
- It overrides the built-in requirement to control access to modules.
Source: GitHub
What to do next?
- All users, package maintainers, and software developers who use the VM2 library for projects are recommended to upgrade to version 3.9.17, which addresses the security flaw.
Beware: The supply chain’s intricacies that impact most open-source software initiatives may hinder the VM2 upgrade process. This makes many users vulnerable to risks for a long period.
Also, it is still uncertain if these vulnerabilities are completely novel or arise due to incomplete fixes for CVE-2023-29017, uncovered by Wi.
Concluding thoughts
The discovery of multiple Sandbox escape vulnerabilities in VM2 highlights the importance of securing open-source software. Individuals and organizations need to be vigilant and take steps to mitigate the risk. The responsibility falls on everyone’s shoulders, who is involved in developing and deploying such tools.



