ScarCruft, a North Korean threat actor, began experimenting with large LNK files to deliver RokRAT malware in July 2022. This was the same month macros were blocked across Office documents by default.
Modus Operandi: Evolving with time
Check Point, a cybersecurity company, explained in a recent technical report that while RokRAT has mostly stayed the same over the years, its deployment methods have evolved.
ScarCruft now uses
- archives containing LNK files that initiate multi-stage infection chains to distribute the malware. This is part of a significant trend in the threat landscape, where advanced persistent threats (APTs) and cybercriminals attempt to overcome the blocking of macros from untrusted sources.
“ROKRAT has not changed significantly over the years, but its deployment methods have evolved, utilizing archives containing LNK files that initiate multi-stage infection chains. This is another representation of a major trend in the threat landscape, where APTs and cybercriminals attempt to overcome blocking macros from untrusted sources. The first sample we will discuss below was discovered in July 2022, the same month Microsoft began enforcing this new rule.”
Destructive abilities
ScarCruft is also known by other names such as APT37, InkySquid, Nickel Foxcroft, Reaper, RedEyes, and Ricochet Chollima.
- The group targets South Korean individuals and entities with spear-phishing attacks designed to deliver a range of custom tools.
- ScarCruft is overseen by North Korea’s Ministry of State Security (MSS), which is responsible for domestic counterespionage and overseas counterintelligence activities.
- The group primarily uses RokRAT (aka DOGCALL) as its malware of choice, which has been adapted for other platforms such as macOS (CloudMensis) and Android (RambleOn), indicating that the backdoor is actively developed and maintained.
- RokRAT and its variants are capable of credential theft, data exfiltration, screenshot capture, system information gathering, command and shellcode execution, and file and directory management.
- The collected information, some of which are stored as MP3 files to cover its tracks, is sent back using cloud services such as Dropbox, Microsoft OneDrive, iCloud, and Yandex Cloud to disguise the command-and-control (C2) communications as legitimate.
ScarCruft also uses
- Chinotto, BLUELIGHT, GOLDBACKDOOR, Dolphin, and, most recently, M2RAT.
- It also employs commodity malware such as Amadey, a downloader that can receive commands from the attacker to download additional malware to confuse attribution.
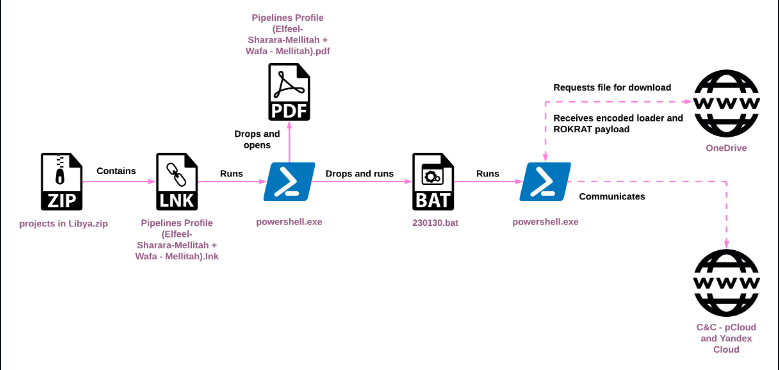
Chain Analysis, Source: Checkpoint
“Recently, ScarCruft has been using LNK files as decoys to activate the infection sequences. The files contain PowerShell commands that deploy the RokRAT malware. While this change in operation signals the group’s efforts to keep up with the shifting threat ecosystem, it continues to use macro-based malicious Word documents as recently as April 2023 to drop the malware. This mirrors a similar chain reported by Malwarebytes in January 2021.”
Wrapping up…
The notorious threat actors in Korea have evolved with time. This could lead to attacks worldwide. The groups have stopped relying on malicious documents, which is a clever move; instead, they have used a hidden file. This means we must be smart enough to combat the phishing attacks.



