A recent malware campaign has been discovered that exploits the Satacom downloader as a means to deploy discreet malware capable of stealing cryptocurrency by using a deceptive extension for Chromium-based web browsers.
According to Kaspersky researchers Haim Zigel and Oleg Kupreev, “the primary objective of the malware delivered by the Satacom downloader is to steal Bitcoin (BTC) from victims’ accounts through web injections into targeted cryptocurrency websites.”
The campaign focuses on users of popular platforms such as Coinbase, Bybit, KuCoin, Huobi, and Binance, primarily in Brazil, Algeria, Turkey, Vietnam, Indonesia, India, Egypt, and Mexico.
Can we link it to the past?
Initially observed in 2019, the Satacom downloader, also known as Legion Loader, acted as a dropper for subsequent malicious payloads, including information stealers and cryptocurrency miners.
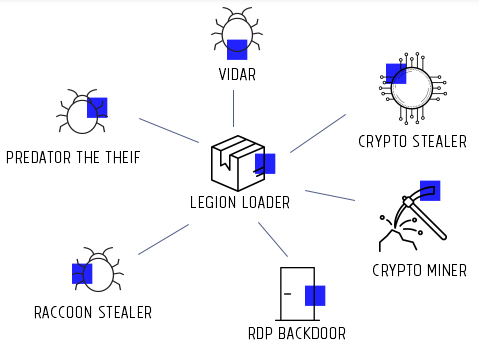
Source: Deep instinct
The prodigy of attack
- The infection starts when individuals searching for cracked software are redirected to fake websites hosting ZIP archive files containing the malware.
The researchers explained that “various types of websites are employed to distribute the malware, including malicious sites with hardcoded download links and legitimate ad plugins injecting a “Download” button.”
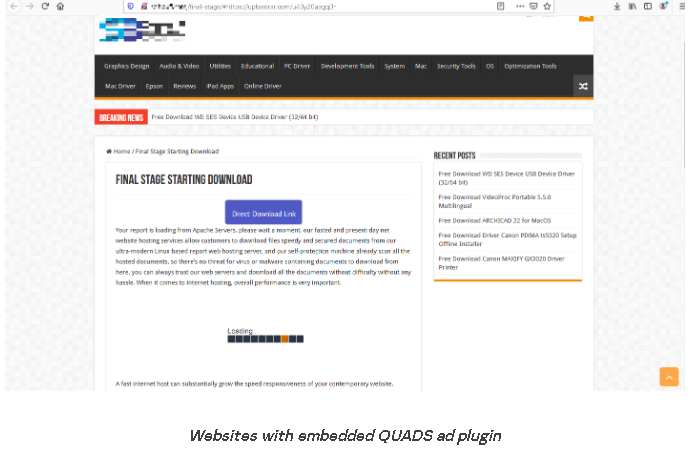
Source: SecureList
- Inside the archive file is an executable named “Setup.exe,” approximately 5 MB in size. The file is inflated with null bytes to evade detection and analysis, making it around 450 MB in total.
- Upon execution, the malware performs its routine, activating the Satacom downloader, which utilizes DNS requests as a command-and-control (C2) mechanism to retrieve the URL hosting the actual malware.
Source: Plato Alto Network
Kaspersky’s deep dive
In the campaign detailed by Kaspersky, as a first step
- a PowerShell script is involved, which downloads the browser add-on from a third-party remote server.
- It searches for browser shortcut (.LNK) files on the compromised system. It modifies the “Target” parameter by adding the “–load-extension” flag, allowing the browser to launch with the downloaded extension.
Second step
The malicious extension disguises itself as a Google Drive extension. It utilizes web injections sent by the C2 server when the victim visits one of the targeted cryptocurrency websites, enabling the manipulation of content and theft of cryptocurrencies.
Third step
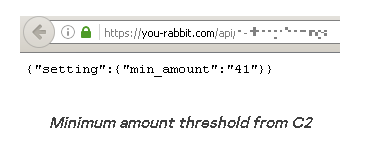
The C2 address remains hidden within the script and addr fields of the most recent Bitcoin transaction linked to a wallet address controlled by the threat actor. This technique is similar to the Glupteba botnet malware, enabling the malware to bypass domain blockades or takedowns.
What’s most nefarious about it?
The researchers stated that
- The extension performs various actions on the victim’s account, remotely controlling it through web injection scripts. Ultimately, the extension attempts to withdraw the stolen BTC to the threat actors’ wallet.
- To further conceal its activities, the malicious extension contains scripts to prevent email confirmations of fraudulent transactions from being seen by the victim. This is accomplished through HTML code injection into Gmail, Hotmail, and Yahoo! services.
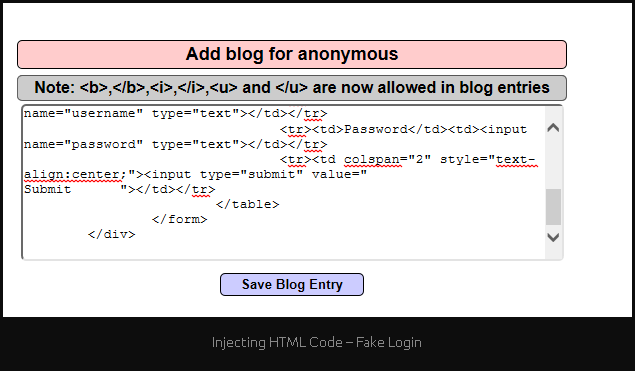
Source: Pentest Lab
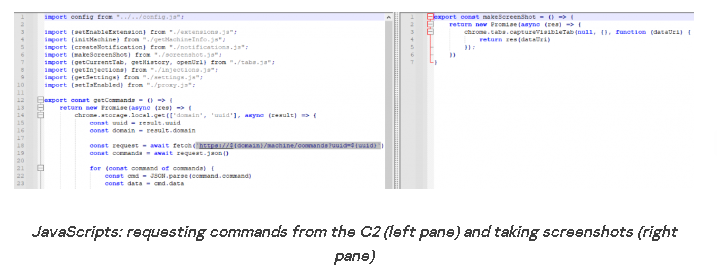
- Another noteworthy feature of the extension is its ability to extract system metadata, cookies, browser history, screenshots of open tabs, and receive commands from the C2 server.
The researchers explained that “the extension can update its functionality by retrieving the C2 server through the last transaction associated with a specific BTC wallet. This allows the threat actors to change the domain URL to a different one if it becomes blocked or banned by antivirus vendors.”
The wholly hidden way to target
This development coincides with discovery of several malicious extensions on the Chrome Web Store. These extensions, masquerading as legitimate utilities, can spread adware and hijack search results, displaying sponsored links, paid search results, and potentially malicious links.
Although these extensions offer the promised functionalities, they contain obfuscated code that allows a third-party website to inject arbitrary JavaScript code into all websites users visit without their knowledge.
Source: Kaspersky
Final thoughts: Protect yourself from the ever-evolving threat landscape
Satacom, due to its nature as a browser extension, can be installed on Chromium-based browsers across different platforms. Although the installation process and infection chain outlined in this article pertain specifically to Windows, if the threat actors target Linux and macOS users, they can easily do so if the victims use Chromium-based browsers.
Be safe, and keep learning!



