Cryptocurrency is often touted as self-custody money, but that promise only works if you keep your keys and passwords secure. Unfortunately, one of the most common ways hackers break into crypto wallets isn’t through fancy Blockchain math or network breaks, it’s through something simple: leaked passwords.
In this guide, we’ll walk through how leaked passwords end up online, how attackers turn those leaks into wallet takeovers, real-world experiences from the crypto community, and what steps every crypto holder can take to stay safe.
Why Leaked Passwords Matter for Crypto Wallet Security
Passwords are the front gate to your digital assets. Even if your wallet’s software and blockchain network are secure, if a hacker gets hold of your login credentials or seed phrase, they can transfer funds without consent or recourse.
This is dramatically different from traditional bank systems where there might be insurance or reversal options. In cryptocurrency, lost or stolen keys mean irreversible loss.
How Leaked Credentials Turn Into Wallet Access
It may sound simple, but there’s a whole underground economy and methodology built around turning stolen credentials into financial theft. Here are the key techniques:
Credential Stuffing Attacks
Credential stuffing is one of the most prevalent methods attackers use to turn leaked passwords into account takeovers.
- Attackers compile lists of leaked email/password combos from breaches.
- They then automate login attempts across many platforms, including cryptocurrency exchanges, wallet services, and email providers.
- These tools test thousands or millions of combinations in minutes to see what works.
This works so well because many people reuse the same password across multiple accounts, an 81% reuse rate has been documented in user surveys.
Victims of credential stuffing may be unaware of the leak, the breach could have originated from any service they signed up for years ago.
Phishing and Fake Websites
Another vector is phishing, hackers set up convincing copies of legitimate wallet login or exchange websites. Then they:
- Trick users via email or social media to enter their password.
- Capture the credentials in real time.
- Use those credentials immediately to drain wallets.
Recent phishing kits have become incredibly sophisticated, targeting financial and crypto brands specifically.
Leaked Cloud Data and Unsecured Databases
Sometimes passwords are exposed through improperly secured cloud storage or developer databases that are left open to the public. These leaks can contain sensitive credentials, including email/password pairs tied to financial accounts.
Once such a database is discoverable online, it’s like leaving a master key under the welcome mat for attackers.
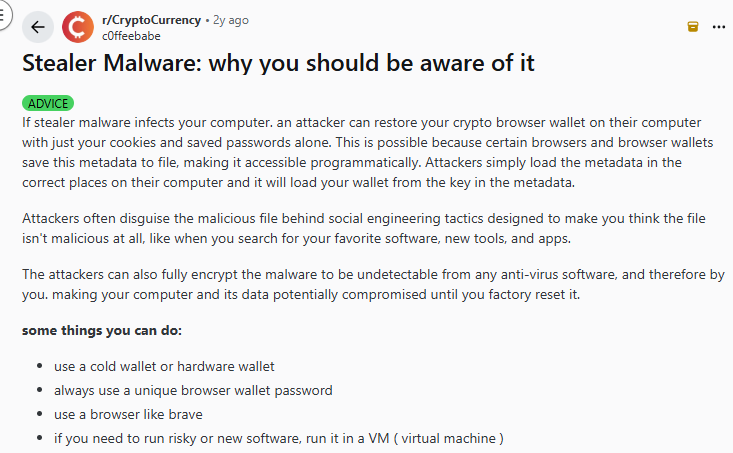
Malware and Stealer Tools
Malicious software known as stealer malware can steal saved passwords, browser cookies, and wallet metadata, effectively giving attackers the same access as the legitimate user.
This malware can be hidden in downloads, pirated apps, or through compromised websites.
Once the malware uploads that data to the attacker, they can access wallets and exchange accounts as though they were the wallet owner.
Real User Experiences: What Crypto Holders Have Reported
Even breaches that don’t directly involve crypto services can empower crimes years later. Take the LastPass 2022 breach: attackers stole encrypted password vaults, and as recently reported, this has enabled ongoing crypto theft totaling around tens of millions of dollars by cracking poorly protected master passwords and accessing seed phrases stored inside.
Victim reports from crypto forums support this trend: users have lost significant funds, tens of thousands to hundreds of thousands of dollars, when seed phrases or login credentials were accessed after being stored in compromised vaults.
In community discussions on Reddit and other platforms:
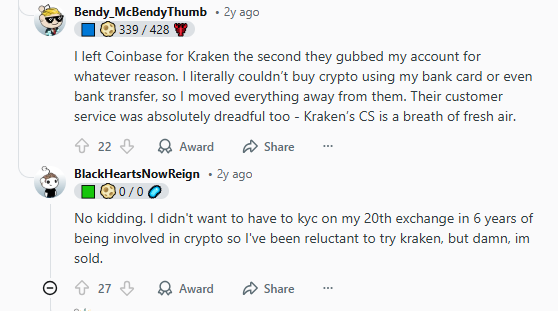
- One user detailed how a hacker gained access to their email, then systematically took over associated Kraken and Binance accounts, despite 2FA being enabled, because the email was the weak link.
- Another shared how stealer malware harvested saved browser cookies and passwords, enabling a wallet to be restored on the attacker’s system.
These accounts show that password leaks aren’t just technical threats, they’re human-experience disasters.
Strong Security Habits for Crypto Wallet Protection
Here’s where we translate the risk into actionable steps every cryptocurrency holder should adopt, whether you’re a beginner or seasoned investor:
1. Use Unique Strong Passwords for Every Service
Never reuse the same password across multiple accounts, specifically between your email, exchange accounts, and any wallet services. If one service is breached, hackers shouldn’t be able to reuse those credentials elsewhere.
2. Use a Secure Password Manager
Managing dozens of unique, complex passwords is tough without help. A password manager securely stores long random passwords behind a master vault, so you never have to remember each one, and this vault is itself protected by a strong master password only you know. While many password managers exist, the important features to look for include:
- Encrypted storage of credentials
- Cross-device syncing
- Auto-generated unique passwords
- Secure backup and reset protections
This kind of secure vaulting helps prevent password reuse and dramatically reduces the chance your crypto access credentials are guessable or compromised.
3. Enable Two-Factor Authentication (2FA)
Adding a second factor, especially using an authenticator app rather than SMS, means that even if a hacker obtains your password, they still can’t log in without the second token.
4. Keep Seed Phrases Offline and Secure
Your recovery seed phrase (the series of 12–24 words that restore your wallet) is the key to your crypto. Never store it digitally, especially not in cloud services, email, or even some password vaults, because online storage can be breached.
Best practice is to write your seed phrase on paper or a dedicated hardware backup and store it offline in a secure physical location.
5. Monitor Breach Alerts and Take Immediate Action
Use services that notify you if your email or credentials show up in known breaches. If you get an alert for any service you use, change that password immediately, and consider updating other accounts that share similar credentials.
6. Leverage a Secure Password Manager
A reputable password manager helps you generate, store, and autofill strong passwords while keeping them deeply encrypted and unique per site. This reduces reliance on memory or simple patterns that are easily leaked or reused.
Rather than saving passwords in browsers or plaintext notes, PureVPN password manager provides:
- Encrypted vaults for all login credentials
- Strong, randomized password generation
- Automated login with no need to remember complex strings
- Alerts when your stored passwords appear in known leaks
Wrap Up
Crypto security isn’t just about keeping your private keys safe but ensuring the credentials never fall into the wrong hands. Leaked passwords are a real and ongoing threat, and attackers use them in automated pipelines to compromise accounts left, right, and center.
Using unique, strong passwords, protecting keys offline, enabling 2FA, and using PureVPN password manager gives you defense against the vast majority of threats.
Frequently Asked Questions
Yes, if hackers can obtain credentials or get you to enter your password on a fake site, they can log into services that control or recover wallets. This is one of the most common real-world attack vectors.
The blockchain itself is secure, but the access keys and credentials are what control your assets. Compromise those, and attackers can move funds irreversibly.
Leaks provide real usernames and passwords leaked from existing services, while brute force is an attacker guessing combinations. Leaks are often easier for attackers to monetize because they already know valid credentials.
Absolutely. Two-factor authentication adds a second block even if passwords are stolen or leaked.
No. Treat your seed phrase like cash, only store it offline and never within internet-connected systems.








