Credential Stuffing – A comprehensive guide
It seems like everyday cyber attackers are coming up with more and more sophisticated techniques to break into systems and steal our intellectual property. With about 193 billion Credential Stuffing attacks in 2020 alone, this particular cyberattack is definitely an A-lister. If you have no idea about what Credential Stuffing is, then we have got everything covered for you. Here is all you need to know about Credential Stuffing:
What is Credential Stuffing?
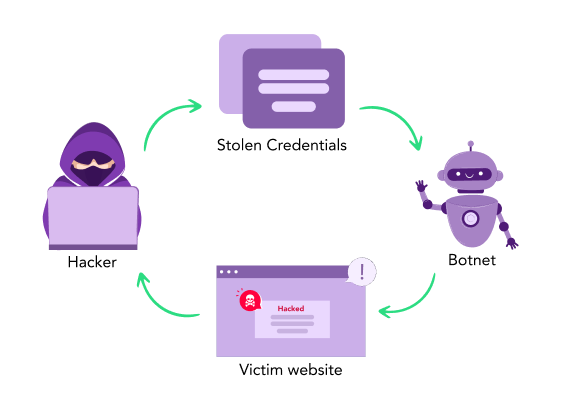
Credential or Password Stuffing is a type of Brute Force Attack. As is apparent by its name, Credential Stuffing utilizes user credentials (username, passwords, etc.) to gain unauthorized access to different platforms owned by the said user.
Credential Stuffing is a single dangerous loop:
-
The attackers get their hands on lists containing information about user credentials.
-
These credentials are then used to break into systems to gather even more sensitive details.
-
The gathered information is then sold to the highest bidder on the infamous dark web.
-
This sensitive information is then used to successfully carry out large-scale security breaches.
And just like that, the loop repeats on and on.
Credential Stuffing – How does it work?
In Password Stuffing, the attacker bases their attack upon the sole hypothesis that a user would reuse their password across multiple platforms. Hence, in a large-scale Credential Stuffing attack, the hacker uses the assistance of automated bots to breach multiple platforms parallelly. Simply put, the process for Credential Stuffing can be defined as follows:
-
The cybercriminal feeds the credential list to an automated bot.
-
This bot simultaneously tries to access multiple platforms using the credential pair.
-
The attacker then monitors the status of the Credential Stuffing attack.
-
Once the bot finds a site where the particular pair works, the attacker then gains access to the user’s data.
This data can now be used for various purposes. From phishing attacks to e-commerce frauds to downright re-selling of sensitive information (account credentials, credit card numbers, etc), Credential Stuffing can quickly take the form of your worst security nightmare!
Credential Stuffing Attacks vs. Brute Force Attacks
Credential Stuffing Attacks
-
- Credential Stuffing is a subset of Brute Force attacks.
- In Credential Stuffing, the attacker already knows the password.
- Use MFA to reduce the threat of a Credential Stuffing attack.
Brute Force Attacks
-
- Brute Force makes up an independent class of cyber security attacks.
- In Brute Force, an attacker tries to guess a password.
- You can specify a limit for failed login attempts to minimize the danger of a Brute Force attack.
How to prevent Credential Stuffing attacks?
Well, all hope isn’t lost. There are still methods with which you can defend your information against such destructive Credential Stuffing attacks. Check out the comprehensive list of preventative measures against Credential Stuffing:.Unique password
Credential Stuffing mainly thrives upon the use of a single password for multiple accounts. Perhaps the simplest solution is to use different credentials for different platforms. Further, refrain from using your email ID as your account for logging into sites.Multi-Factor Authentication (MFA)
This method provides an effective solution against Credential Stuffing attacks. This multi-factor authentication technique uses access tokens, biometric identification, one-time codes, etc.Limit traffic and ban IPs:
A site can become a victim of Credential Stuffing if most of its traffic is coming from bots. In that case, you need to block suspicious IPs to limit bot traffic. Further companies can also use bot management services which help with filtering out bot traffic to protect against Credential Stuffing.Passwordless authentication
This form of authentication is effective against Credentials Stuffing attacks as they do not need an alphanumeric string for login. Instead, they rely upon possession or an object that can uniquely identify a person.CAPTCHA
Using a technique like CAPTCHA can keep the bots at bay but it needs to be used alongside other stronger authentication techniques. Apart from these, you can also use methods like credential hashing or continuous authentication techniques to further protect your accounts against Credential Stuffing.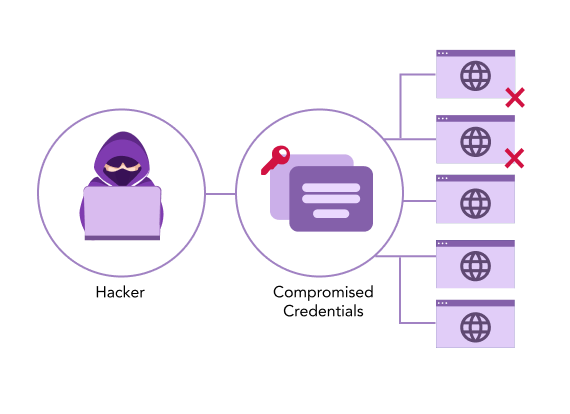
Learn more about DDoS
- What is a DDoS Attack?
- How to Prevent DDoS Attack on Xbox
- Blackhole Routing
- HTTP Flood Attack
- Cross site Forgery Attack
- Malicious Payload
- HTTP Vulnerability
- What is Password Spraying
- DNS Flood Attack
- Low and Slow Attack
- What Happens During a DDoS Attack
- SSDP DDoS Attack
- Smurf DDoS Attack
- DDoS Botnets
- UDP Flood Attack
- Slowloris Attack
- NTP Amplification Attack
- DDoS Mitigation
- Ping Flood Attack
- DDoS Booter
- DNS Amplification Attack
- Brute Force Attack
- Golden Ticket Attack
- Credential Stuffing Attack
- How to Prevent DDoS Attack on Router
- Memcached attack
- Application Layer DDoS Attack
- DDoS Attack Prevention
- BGP Hijacking
- IP Fragmentation Attack