Table of Contents
If your organization is looking for a way to effectively manage security risks and adopt best practices, the NIST cybersecurity framework is for you!
It combines different aspects of modern security management and provides comprehensive and clear guidelines to help mitigate cyber threats.
In this blog, we will look closely at the NIST CSF and how your organization can implement this effectively. Let’s get started:

NIST – A brief history of the Cybersecurity Framework
After Target suffered one of the worst retail data breaches in 2013 followed by countless attacks on several major organizations, including Sony Pictures, cybersecurity institutes wanted to create easy-to-comprehend security guidelines to better manage such threats.
So in 2013, the National Institute of Standards and Technology (NIST) closely worked with the U.S. private sector to make standard security practices that organizations can follow to mitigate security risks. And this is exactly how the Cybersecurity Framework Version 1.0 came about.
What is exactly the NIST Cybersecurity Framework?
Simply put, the NIST cybersecurity framework is a crucial tool that provides organizations with best practices to build and improve their cybersecurity program. Businesses of varying sizes can use this framework to detect and mitigate security threats.
The NIST CSF helps set a security standard across all industries to combat the ever-growing threats. To better understand the structure, we can break it down into three main parts:
- The core
- The tiers
- The profiles
Source: NIST
Let us explore each in a little more detail:
- The core structure of the NIST cybersecurity framework
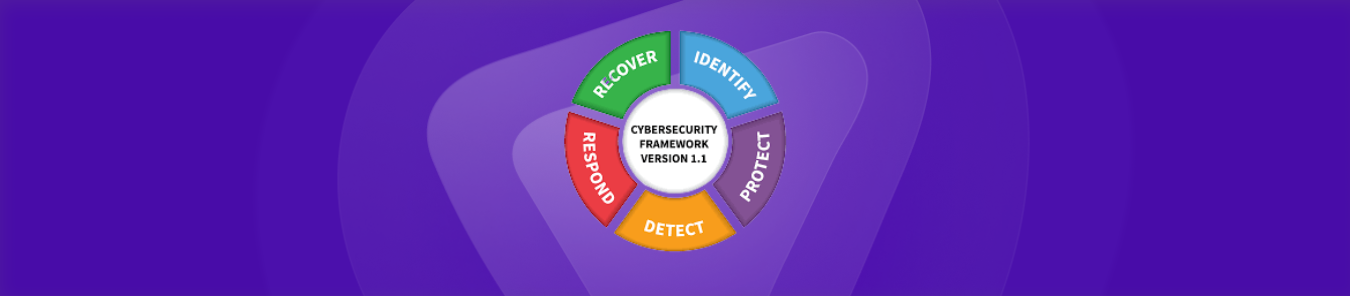
The core provides the general idea of how to manage and maintain cybersecurity processes at organizations. So, What are the 5 areas of the NIST Cybersecurity Framework? Here they are:
Identify
This function helps organizations identify the assets, operations, and business environment that needs protection. It also helps with risk assessment and supply chain risk management by identifying vulnerabilities that can threaten an organization’s infrastructure. It all boils down to creating effective policies and strategies to help identify and mitigate security risks.
Protect
This function involves implementing security policies, strategies, and best practices to protect critical infrastructure. Access control, security awareness training, maintenance, backups, and other security technologies like encryption are crucial parts of this function.
Detect
This activity involves continuously monitoring activities and events to detect any anomalies and security threats so that they can be dealt with efficiently. It also helps to verify the effectiveness of the cybersecurity best practices and measures already in place.
Respond
This activity involves how organizations should respond and reduce the impact of a cybersecurity attack. The response planning process, analysis, efficient communication, effective mitigation techniques, and improvements are crucial parts of the response activity.
Recover
This activity involves the recovery planning phase to implement cyber resilience. It can ensure that a business can quickly recover from a security attack and restore assets and operations affected by the attack.
Source: NIST
- Tiers of NIST cybersecurity framework
The tiers of the NIST cybersecurity framework help organizations and businesses evaluate their progress when it comes to implementing cybersecurity best practices:
Tier 1 [Partial]
At this level, an organization has limited awareness regarding cybersecurity best practices and has more of an ad-hoc approach when it comes to responding to security threats. It means that an organization usually deals with security risks once they show up and struggles to effectively mitigate such threats.
Tier 2 [Risk Informed]
At this level, an organization has some ideas and strategies in place regarding cybersecurity risks. However, it doesn’t have a repeatable risk management process used in case of an attack.
Tier 3 [Repeatable]
At this level, an organization will have a routine or a repeatable risk management process to evaluate and patch up its vulnerabilities. The business is aware of the various cybersecurity threats and can efficiently respond to them.
Tier 4 [Adaptive]
At this level, the organization is essentially resilient to cyber-attacks and spends significant resources on continuously improving its risk management process. They have policies, standards, and strategies to adapt to the ever-growing cyber threat risk.
Source: NIST
- Profiles of NIST cybersecurity framework
The NIST profiles help organizations determine where they stand concerning their cybersecurity end goals.
Current Profile
An organization’s current profile determines the present state and reliability of its risk management processes. This profile can be effectively gathered via security assessments and active analysis to help stakeholders understand how strong your defenses are right now.
Target Profile
The target profile is where you see your organization’s cybersecurity in the future. It provides us with a path to work with to develop more effective cybersecurity processes to achieve our end goal.
Gap Profile
The gap profile is made by analyzing the difference between the current and the target profiles. Simply put, it equals the work you need to put in to make up for this gap in your defenses to activate your desired cybersecurity level.
How to better manage risk with the NIST framework?
NIST also guides organizations provides on how to effectively integrate the cybersecurity framework to help build repeatable and effective risk management programs:
Prioritize/Scope
The first step calls for businesses to set up objectives, needs, and security demands. It will help them get a clear idea regarding their cybersecurity program and prioritize more critical areas.
Orient
The next step involves a detailed analysis of the organizational resources and operations to develop processes and strategies to counter potential cyber security threats.
Current profile
The third step encourages organizations to develop a current profile which will help them analyze where their security practices and risk management processes stand currently.
Risk assessment
After a current profile is made, businesses must conduct risk assessments to evaluate the efficiency of their threat prevention and management systems. It will also help these businesses analyze just how badly a cyber threat can affect their operations.
Target profile
As explained above, a target profile helps businesses set up goals when it comes to effectively managing the risk management processes.
Gap analysis
The gap analysis helps companies understand the difference between their current cybersecurity management policies and their security goals.
Action plan
After gap analysis, companies can effectively come up with a detailed action plan to achieve their cybersecurity goals and implement best security practices in their organizations. This plan includes everything from milestones to resources.
NIST Cybersecurity Framework 2.0: An update?
In 2023, NIST released a 2.0 draft version of its cybersecurity framework which updated the CSF’s scope to include businesses of all forms and sizes. Further, the 2.0 update also added a new function to the core of the framework – Govern. The discussion draft defines the new function as:
“Cybersecurity governance through a new Govern Function covering organizational context, risk management strategy, policies and procedures, and roles and responsibilities.”
This function will mainly help organizations devise better policies, procedures, and risk-management techniques to effectively lead the organization toward improved cybersecurity infrastructure.
Bottom line: Why use the NIST Cybersecurity Framework?
The thing about managing cybersecurity is that most of the time organizations are not aware of the vulnerabilities and security risks attached to their day-to-day operations. Later, these vulnerabilities become weak spots that are often overlooked but not by attackers!
Therefore, to efficiently manage a risk management process, achieve cybersecurity goals, and successfully protect data against security threats, companies must understand the importance of this standardized tool.
All in all, the NIST CSF, provides companies of all sizes with easy means to integrate efficient technology and mechanisms to counter modern-day cybersecurity attacks.