Encryption is one of the most important things a VPN does, but most people never really see what’s happening behind the scenes. You know your data is being secured, yet how that protection actually works, isn’t always obvious.
If you’ve ever wondered how a VPN keeps your information private, whether or not it encrypts everything you do online, or how to confirm that your connection is actually secure, you’re in the right place.
In this guide, you’ll understand how VPNs encrypt your data, how strong that protection really is, and what parts of your online activity remain visible even when a VPN is turned on:
What does VPN encryption actually mean?
VPN encryption is the process of turning your readable online data (such as the websites you visit, the messages you send, or the files you download) into unreadable code before it leaves your device.
Once encrypted, your data looks like random noise to anyone trying to intercept it, whether that’s your Internet Service Provider (ISP), someone on public Wi-Fi, or a cybercriminal monitoring the network.
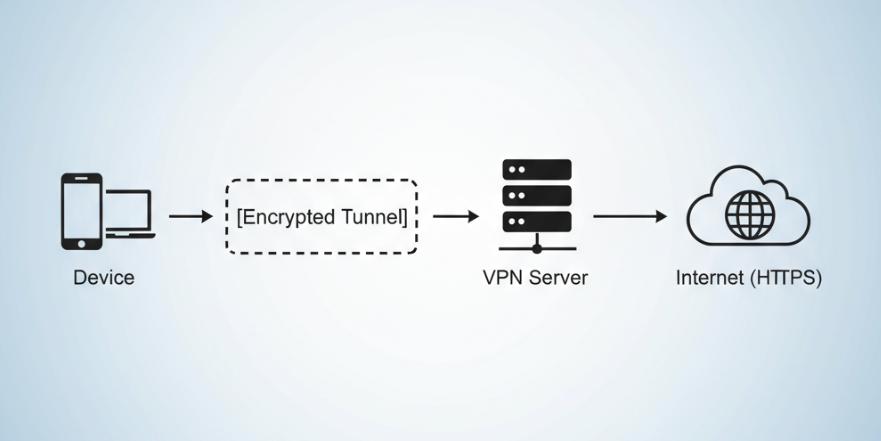
When you connect to a VPN, your device and the VPN server establish a secure, encrypted tunnel. All your traffic travels through it, meaning only the VPN server can decrypt your information and deliver it to the internet.
This protects your browsing activity, IP address, and online identity from being monitored or exposed while the data is in transit, keeping prying eyes from seeing what you’re doing online or tying your activity back to you.
How do VPNs ensure end-to-end encryption?
A VPN ensures end-to-end encryption by securing the connection between your device and the VPN server through a few key steps:
- Secure authentication: Your VPN app first confirms that the server you’re connecting to is genuine by checking its digital certificate. This prevents man-in-the-middle attacks and ensures you’re communicating with the correct endpoint.
- Key agreement: Your device and the VPN server then use cryptographic methods like Elliptic Curve Diffie–Hellman to generate temporary session keys that only the two endpoints can use to encrypt and decrypt your data.
- Encrypted tunnel creation: After the keys are agreed upon, the VPN protocol (such as OpenVPN, WireGuard, or IKEv2) establishes a private, encrypted tunnel. From this point on, all traffic between your device and the VPN server is fully protected.
Once this tunnel is active and running, everything you send or receive travels through it as encrypted ciphertext. Your ISP can see that you’re connected to a VPN, but not what websites you visit or what data you’re exchanging.
Anyone on public Wi-Fi may detect your connection, but they can’t read or tamper with any of the information inside it. Together, these protections create a fully encrypted path from your device to the VPN server, so your online activity stays protected.
How VPNs handle data encryption keys
VPNs use encryption keys to keep your data private, but these keys aren’t permanent or reused across sessions. Instead, modern VPNs generate, rotate, and destroy them in a way that protects your information even if someone manages to intercept encrypted traffic.
When you connect to a VPN, your device and the VPN server create short-lived session keys through a secure key-agreement process. These keys are unique to your connection and exist only in temporary memory, so they can’t be recovered or reused later.
Modern VPN protocols use Perfect Forward Secrecy (PFS) to regularly refresh encryption keys during the session, preventing any captured traffic from being decrypted afterward. Even if someone recorded your encrypted data, each portion would require a different key, and none of those keys exist once the session ends.
Throughout this process, the keys themselves never travel across the internet in raw form. They’re derived independently on both ends using cryptographic methods like ECDH, used only for the duration of the session, and automatically wiped when the connection closes.
These practices ensure that each VPN session is completely isolated from the next. The moment your keys disappear, so does any chance of decrypting your past activity, keeping intercepted data useless to anyone trying to access it.
Does VPN encrypt traffic from all apps?
A VPN encrypts all traffic that leaves your device and is sent to the internet, regardless of which app generates it. As long as an app uses your device’s standard network connection, its data is routed through the VPN tunnel and protected by encryption.
However, there are a few cases where traffic may not pass through the VPN:
- Traffic that stays on your local network: Connections to nearby devices, such as printers, smart TVs, or local file sharing, don’t leave your network and therefore don’t use the VPN tunnel.
- Traffic coming from certain system-level services: Some operating system background processes may not always use the VPN tunnel depending on how your device handles system traffic.
- Traffic excluded through split tunneling: If you’ve configured your VPN to allow specific apps to bypass the VPN, those apps will connect directly rather than through the encrypted tunnel.
- Traffic leaks caused by misconfigurations: DNS leaks, IPv6 leaks, or WebRTC requests can escape the VPN tunnel if the VPN app doesn’t block or reroute them.
Outside of these exceptions, a properly configured VPN encrypts essentially all internet-bound traffic from your apps. If an app requires an internet connection, and the VPN is active, its traffic will normally pass through the encrypted tunnel.
What’s the difference between SSL and VPN encryption?
SSL/TLS and VPN encryption both protect your data, but they work in different ways and cover different parts of your online activity. SSL/TLS is the technology behind the padlock icon you see in your browser. It secures the connection between your device and a specific website for things like banking or shopping. Its protection is limited to that one website session.
A VPN works at a broader level. Instead of encrypting just browser traffic, it encrypts all internet-bound data from your device. That includes things like streaming apps, email clients, messaging apps, and software updates. All of that goes through the encrypted VPN tunnel, regardless of whether individual websites use HTTPS or not.
The path of encryption is also different. SSL/TLS protects data only between your device and the website you’re visiting. A VPN protects data between your device and the VPN server. Beyond that point, your traffic is only encrypted if the website itself uses SSL/TLS. When both are active, your data stays encrypted from your device all the way to the website.
| Feature | SSL/TLS | VPN Encryption |
| Scope of protection | Browser-based (website-specific) | Entire device (all internet traffic) |
| Encryption path | Device > website | Device > VPN server |
| App coverage | No (browser only) | Yes (all apps using the internet) |
| Requires website support | Yes (HTTPS required) | No (works regardless of website) |
| IP address exposure | Real IP visible to websites | Websites see VPN server IP |
| Visibility to ISP / local network | ISP can see destination sites and DNS | ISP sees only VPN server; destinations hidden |
| Primary purpose | Secure logins and transactions | Full traffic protection and IP masking |
How do I know if my VPN is really encrypting my data?
A VPN only encrypts your data when the encrypted tunnel is active, so the easiest way to confirm encryption is to check whether all your traffic is moving through that tunnel. Here’s how to verify it:
- Check your public IP address: Visit an IP lookup site after connecting to the VPN. If you see the VPN server’s IP instead of your real one, the encrypted tunnel is active. If your real IP still appears, encryption isn’t applied.
- Test your DNS requests: Run a DNS leak test. With proper encryption, all DNS lookups should be routed through the VPN’s DNS servers. If your ISP’s DNS appears, part of your traffic is escaping the tunnel.
- Check for WebRTC leaks: Take a WebRTC leak test in your browser. If it shows your VPN IP, your browser is routing WebRTC requests through the encrypted tunnel. If it shows your real IP, those requests are bypassing encryption.
- Confirm connection status: Most VPN apps display when an encrypted tunnel is successfully established. If your app shows you as “connected” and assigned a VPN IP, your data is being encrypted.
What kind of encryption do top VPNs use today?
Modern VPNs use two primary encryption ciphers to protect your data inside the VPN tunnel: AES-256 and ChaCha20-Poly1305. These are the ciphers supported by today’s most trusted VPN protocols and are widely used across top VPN providers, including PureVPN. Let’s take a closer look at them:
AES 256 (OpenVPN and IKEv2/IPSec)
AES-256 has been the gold standard in VPN security for many years now. It’s extremely secure, resistant to brute force attacks, and benefits from hardware acceleration on most modern CPUs. This makes it fast and reliable on desktops, laptops, routers, and other high-performance devices.
Key advantages of AES 256:
- Long-proven and heavily audited
- Excellent performance on hardware with AES acceleration
- Trusted in government, enterprise, and military-grade systems
- Strong confidentiality and authenticated encryption (via GCM)
ChaCha20-Poly1305 (WireGuard)
ChaCha20-Poly1305 is designed for speed and security on all device types, especially mobile devices and CPUs without AES acceleration. It offers the same level of protection as AES-256 but performs better on smartphones, tablets, and low-power hardware. Its smaller, cleaner codebase also reduces the risk of implementation flaws.
Key advantages of ChaCha20-Poly1305:
- Faster than AES on mobile and ARM processors
- Highly efficient for battery-powered and low-power devices
- Modern, minimal codebase with lower attack surface
- Built-in integrity validation through Poly1305
Frequently asked questions
VPN certificates and encryption keys help your device verify that it’s connecting to a legitimate VPN server and not an impostor. The certificate proves the server’s identity, while the keys are used to securely establish an encrypted session.
You can check your VPN’s encryption level by looking at the protocol your app is using. OpenVPN and IKEv2 typically use AES-256, while WireGuard uses ChaCha20-Poly1305. Most VPN apps display the active protocol and encryption mode in the connection details or settings menu.
256-bit encryption refers to the size of the key used to secure your data. A 256-bit key offers an enormous number of possible combinations, making brute force attacks practically impossible. In VPNs, this usually means AES-256, a cipher widely trusted for strong, long-term security.
A VPN routes your DNS requests through the encrypted tunnel so they’re handled by the VPN’s own DNS servers instead of your ISP’s. This keeps the websites you look up private and prevents DNS leaks, ensuring your browsing history isn’t exposed on the network.
A VPN handshake is the process where your device and the VPN server authenticate each other and agree on the encryption settings for the session. During this negotiation, both sides select the cipher, generate shared keys, and establish the secure tunnel that protects your traffic.
Final word
VPNs turn your data into unreadable ciphertext and send it through a secure tunnel, protecting your identity, browsing, and IP address from anyone trying to monitor your connection. With modern ciphers like AES-256 and ChaCha20, a well-configured VPN keeps your data safe on any network, including public Wi-Fi.





