Table of Contents
We’ve all read stories of people getting hacked and thought that this would never happen to us. Sometimes, it’s hard to imagine why someone would dedicate their time and resources to hacking ordinary people like us when they can just go on and hack a celebrity or a business and steal a lot more in the process.
But hackers are smart, and they understand the difficulties and risks associated with hacking high-profile celebrities or businesses. So instead, they target ordinary people like us because we are easy targets. And then, one day, when we are targeted, there’s nothing we can do except learn an important lesson: Nobody is safe from getting hacked.
The answer is Yes. Read through the guide below to learn the different methods hackers use to hack someone and how to avoid getting hacked.

Let’s start with a story
John, a freelance writer, was once scrolling through his phone when he received an email from what appeared to be his bank. It stated that the bank had detected suspicious activity and asked him to verify his account details to stay safe. John entered his login credentials without thinking much about it and was redirected to another page that thanked him and logged him out.
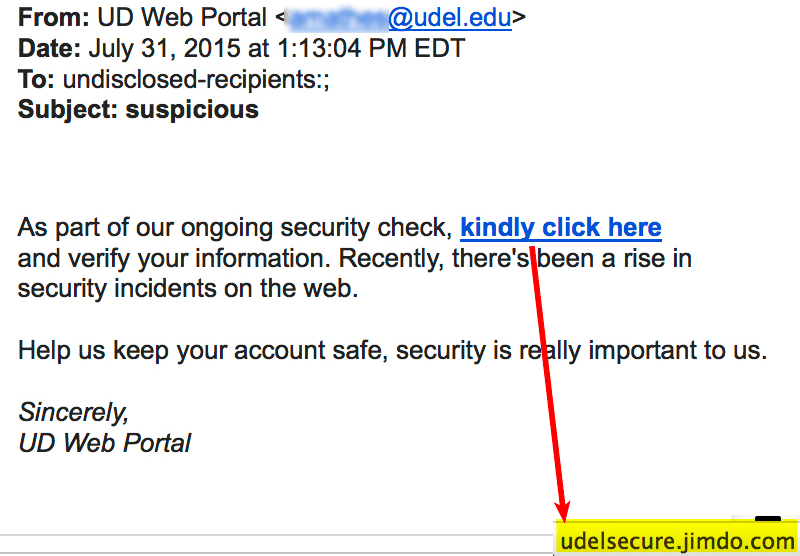
Source: University of Delaware
A few days later, John noticed several withdrawals from his bank account. Upon checking, he noticed that much of his money was gone. Panicking, John called his bank, where he was told that the email he had received was most likely a phishing scam and that his account had been hacked and the money stolen by hackers.
All that John could do now was learn from the experience and stay careful against similar hacking attempts in the future.
The easiest way to get hacked: phishing scams
Have you ever received an email or a text message offering a discount that looks too good to be true? Then that’s most likely the case. Offering discounted deals is the perfect hook hackers use to entice anyone to open a suspicious link. These discounts are fake, of course, and when you open the link, you immediately fall into the trap.
The link can either install malware on your device. Or it can route you to a webpage that asks for your personal information, as in the story above so that the hacker can access your accounts.
It’s hard to guess which of the two is worse. For instance, malware can often steal any saved passwords on your system. Or it can take the form of ransomware and lock your system to demand a hefty ransom you must pay to get your files back.
Phishing accounts for a large percentage of all hacking attempts. According to Verizon Data Breach Investigations Report, phishing attacks account for 36% of all data breaches.
How to stay safe from phishing
Phishing is the easiest way for a hacker to hack someone. Turns out, it’s also easiest to avoid. All you need is a little awareness mixed with caution, and you will be able to detect and avoid any phishing scam in the future.
To avoid phishing, you should:
1. Be cautious of all unexpected or unsolicited emails. Ensure to check the sender’s email address before opening any email. And when you open it, try to avoid downloading any file attachments or opening any links unless you’re completely sure about the email’s authenticity.
2. Be wary of entering personal information on websites. We never know if the page we’ve opened is genuine or fake. It’s best to stay cautious and avoid entering details like your name, credentials, email address, or any information related to your bank account.
3. Use spam filters and anti-virus software, which serve as added safeguards against phishing. Even when you do click on any suspicious link, your anti-virus software can still come in handy and protect you from viruses and malware.
Story # 2 – Locked out from your system
Meet Jack, a developer who works freelance for multiple clients. One day, Jack was suddenly locked out of his system while working on an important project. Trying to access the system again didn’t help. Instead, his screen went blank, and the following message popped up: “Your files have now been encrypted. To get them back, you must pay a ransom. Failure to pay within 24 hours will result in the permanent deletion of all your files. “
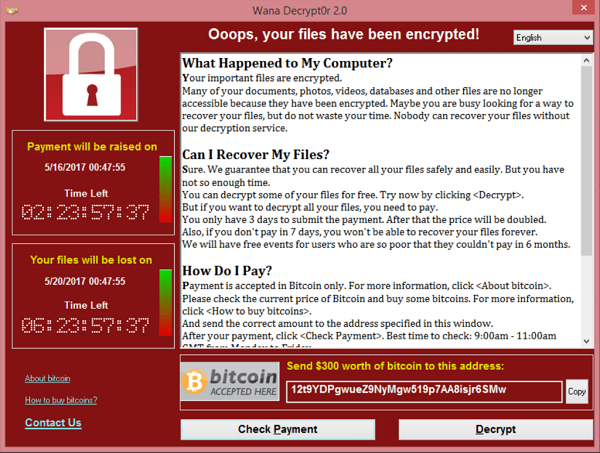
These files were extremely important to Jack and had no backups stored anywhere, and Jack had no other option but to pay the ransom and return the files.
Later, he read in the news that he was not the only person who fell victim to the ransomware attack. One software he was using had a critical bug that the hackers exploited. The software company had already released a security patch that fixed the bug, but many, like Jack, had not updated the app, and all became victims of cybercrime.
Turning off automatic updates is not recommended
It is easy to notice that Jack’s story is similar to countless other stories that happen daily in various parts of the world. No software or application has any vulnerabilities or bugs in it. Hackers work day and night to identify and exploit these vulnerabilities to perform cyber crimes.
Hackers can then either install malware onto the systems and steal any private data that they can get their hands on. Or they can encrypt the files and demand a ransom. There is no end to what they can do to harm the victims.
What can you do to stay secure?
Ref: Quora
Here are a few steps you can take to ensure that you don’t fall into the same trap as Jack did:
1. Always keep your software and operating system updated. These updates often contain security patches for critical vulnerabilities. The most recommended option is to turn on automatic updates so that all bugs are fixed immediately as soon as an update is released.
2. Always keep backups of your important files. Jack could have avoided paying the ransom amount if he had had any backups of his important files. Even if his files got deleted, Jack could have used the backup files to avoid losing any critical data.
Final story – Horror unfolds inside a local cafe
Abigail, a journalist, was running on a tight deadline. Despite pulling off an all-nighter, much work still needed to be done. Exhausted, Abigail decided to head to the local cafe and work from there. She ordered a coffee, connected her system to the cafe’s WiFi, and started working on her article.
After an hour or so, her work was finally done. Sighing with relief, she sent an email containing the article to her editor. Just then, another email dropped by. When she opened it, her happiness vanished in an instant. That email contained an attachment, which was a private picture of Abigail that was for her own eyes only. She had never sent this picture to anyone else. Then why was she receiving this picture in an email from an unknown sender?
The email contained a note. Apparently, the sender had many more private pictures like these, and he was now blackmailing Abigail to send him money. He even had the email address of Abigail’s editor, and he promised that if he was not paid, the editor would be the first to receive these pictures.
All Abigail could do now was panic, listen to what the blackmailer had to say, and comply with his requests.
What happened here?
Abigail made a mistake that we are also prone to making: connecting with a public WiFi network. Public WiFis are notoriously dangerous. You might think that these hotspots have passwords and everything, but a password alone offers little protection to anyone who is connected to the network.
Since anyone can connect to a public WiFi network, hackers often use it to hack inside other computers or smartphones that are connected to the same network. In this case, the hacker was also sitting inside the cafe using the same WiFi network. When Abigail connected, the hacker used the network to hack into her computer and steal all her private photos, which he then used to blackmail her.
How to stay safe on public WiFi networks
The best way to stay safe on public WiFi networks is to use an encrypted VPN service like PureVPN. Services like PureVPN offer end-to-end encryption to users, ensuring their online traffic remains safe and inaccessible. This means that even if your device is connected to a WiFi network that has already been compromised, your data and your online traffic will remain safe from hackers and cybercriminals.
Here are the steps you need to follow to stay safe on public WiFi networks:
- Get PureVPN
- Download the app on any device
- Go secure by connecting to any location from within the app
- Connect to any public WiFi and start browsing!
Conclusion
There are countless ways to get hacked, and the examples and stories mentioned above only represent the tip of the iceberg. Cyber threats are constantly evolving, so you must stay proactive at all times and use every tip and tool at your disposal to stay safe from hacking attempts.
Frequently Asked Questions
Cyber threats include phishing scams, malware, ransomware, and social engineering tactics. Cyber threats are ever-evolving, so it is important to stay updated about any new threats or vulnerabilities.
We do not recommend that you pay any ransom fee after a ransomware attack because there is no guarantee that the hacker will provide you with a decryption key or even if a decryption key actually exists. It’s better to be safe than sorry and create backups of your data to switch to them if a ransomware happens.



